
What’s in a Good Security Risk Assessment?
- On 04/07/2019
If you’ve ever undertaken a security risk assessment (SRA) yourself, you may have wondered whether it was as comprehensive as it could be and if could it withstand serious scrutiny. Part of the notion of completing a diligent risk assessment is to first understand where the rest of the industry is at, so that we can get a measure of the likely credibility of our own work. We can then use this information to continually improve levels of risk competency and product.
Challenges
One of the key challenges in knowing how a SRA stacks up is to be aware of where better practices can be found. It is also true that, while there are some staple components of SRAs, there is some degree of an art in putting them together in a logical fashion.
Whether it be cyber or protective security focused, a good SRA is one that:
- More than adequately tells a story by providing background and sufficient context to the process being undertaken.
- Articulates the compelling reasons as to why change is needed (much like a business case).
- Clearly defines the assets (physical, personnel, operational and intangible etc.) that require protection, and highlights the relative importance of those assets (i.e. through a criticality analysis).
- Describes areas of vulnerability and risk within the organisation, consistent with the scope of the assessment.
- Provides sufficient background to the various threat actors and acts that may impact those assets by way of a threat assessment.
- Identifies the risk controls that are used to protect against those threats, and how effective each of them is at doing so (i.e. a Risk Control Effectiveness assessment).
- Identifies inherent risks and their ratings according to organisational risk criteria (i.e. not criteria supplied by a third party, unless the organisation lacks internal risk management policies and frameworks).
- Examines inherent risks to identify which are beyond tolerable limits.
- Identifies additional, pragmatic and cost-beneficial risk controls that reduce the likelihood of a threat act being successful (resulting in associated risks being realised), or consequence of an incident (through effective response and recovery controls).
- Supports its recommendations through defining the benefits to the organisation, in support of its strategic and operational objectives.
- Considers the SRA process a critically discrete and keystone element of developing a security/risk treatment plan.
- Is monitored, reviewed and updated/improved over time (rather than recreated each period).
It is rare that security risk assessments are quantitative in nature (i.e. using numbers, rather than assessor judgement, to calculate criticality, threat and/or risk ratings). One of the primary reasons for this is the lack of easy access to accurate figures/numbers to make calculations on.
ISO 31000 and security risk methodology alignment
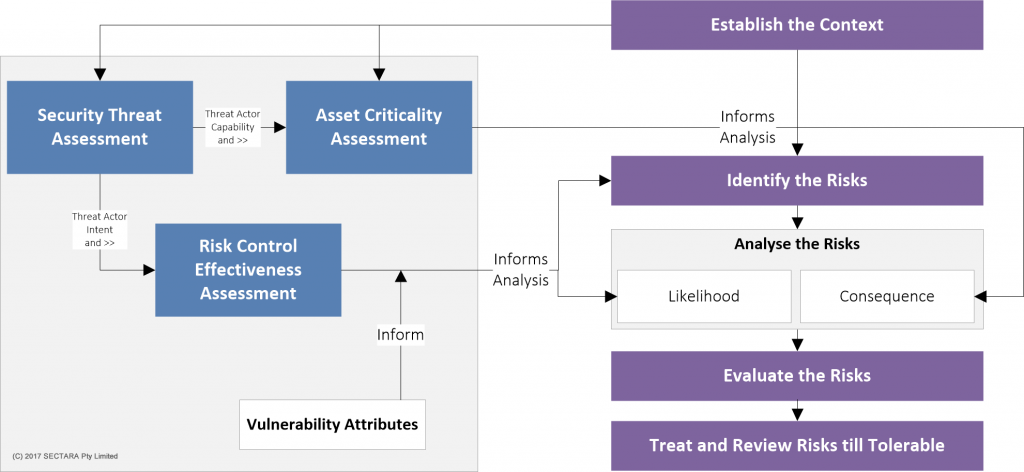
The Security Risk (Assessment and) Management Process
Notable exceptions do exist however; fox example, within the insurance industry it is commonplace to use historical records, demographic data and other inputs to quantitatively assess the likelihood of specific types of crime. Insurance premiums are then based on this potential.
Regardless of the type of SRA that you are undertaking, the risk assessment should at least adhere to the basics detailed above. That way, it will be much more likely that its findings will be accepted, and recommendations successfully implemented.
How SECTARA Uses Good Risk Assessment Practices
Industry Risk has incorporated such approaches within our SECTARA security risk assessment platform. Indeed, our desire to ensure best practice in all aspects of security risk management is what drove us to develop it.
SECTARA requires users to apply the risk assessment matrix in the current risk assessment rating stage, and then commit to a re-assessment of security risks once treatment recommendations have been made.
Learn more on how SECTARA creates useful risk assessment matrix by signing up to our free plan or book a demo to find out more.


